-
-
Recycle Bin Forensics
-
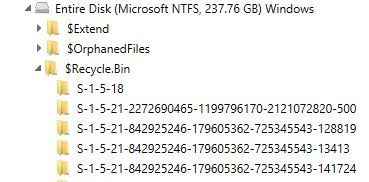
Recycle Bin - Computer Forensics ConsiderationsNo windows computer forensics examination is complete without a review of the recycle bin. Let’s explore its purpose, the recycle bin is a feature of the Windows operating system that allows users to recover deleted files. It was first released in 1995 in Windows 95. When a file is deleted, it is not immediately removed from the hard drive. Instead, it is moved to the recycle bin, where it can be restored if necessary. The recycle bin is a convenient way to undo accidental deletions. If a user accidentally deletes a file, they can simply open the recycle bin and restore the file. This eliminates the need to search for a backup copy of the file or to recreate it from scratch. In addition to providing a way to recover deleted files, the recycle bin also serves as a safety net for users who are unsure about whether they want to permanently delete a file. When a user deletes a file, it is automatically moved to the recycle bin. The user can then decide whether to restore the file or to permanently delete it. The recycle bin is not a perfect solution, however. There are several limitations to its functionality. For example, files that are deleted from a removable drive, such as a USB flash drive, are not moved to the recycle bin. Additionally, files that are deleted using a command line or programmatically are not moved to the recycle bin. Furthermore, the recycle bin has a limited capacity. When the recycle bin reaches its maximum capacity, it will automatically delete the oldest files in order to make room for new ones. This means that there is a risk of losing files if the recycle bin fills up before they can be restored. A computer forensic examination of an info2 file involves analyzing the file to extract and examine the data stored within it. This process can be used to uncover information related to a criminal investigation or to gather evidence in a civil case. The first step in conducting a forensic examination of an info2 file is to identify the file and determine its relevance to the case. This may involve reviewing the file's metadata, such as its creation date and the user who created it, as well as its content. It can be located in different places depending on the host's operating system. Once the file has been identified and its relevance determined, the next step is to extract the file from forensic image. On older Windows versions, this is the info2 file. In newer versions this is done by examining the $Recycle.Bin folder. The data may be analyzed using Axiom, Autopsy or a python script to parse the file and extract the data. In Vista and later (such as Windows 10) there are two important files for a computer forensic examination of the Windows Recycle Bin. For each deleted document, there are two files, which begin with $I and $R files. These files are located within a hidden folder called $Recycle.Bin in the root directory aka c:\. Within this folder, there are subfolders, which are grouped by the user’s SID. The $I and $R files will be located within the SID folder. Here is an example.
Each file contains different information.
During the analysis process, it is important to document all findings. This includes keeping detailed notes on all steps taken during the forensic examination and creating a report detailing the findings of the examination. In summary, a computer forensic examination of an info2 file or the $Recycle.Bin folder involves identifying and creating a forensic copy of the file, analyzing the data it contains, and documenting any findings. This process can be used to gather evidence in a criminal or civil case and can help to uncover information that may be relevant to the investigation. Here is a helpful video with more details. |
|